Hacking and its variations
February 1, 2017
Hacking is the process of gaining access to a computer or data on a computer without permission, and while I am assuredly not an expert when it comes to hacking or anything of the sort I would like to explain it as best I can and give insight received from a good friend of mine.
White Hats: The tech specialists in the industry typically looking to find weaknesses in a website or program to help out the creators, notifying them of their issue without causing any harm usually for payment. I interviewed Jack Groele*, a friend of mine who works as a white hat for a living, informed me about some various aspects of hacking that he was familiar with. When searching for vulnerabilities in varying situations Groele said that “Yeah it is so involved and it doesn’t feel like real life when I am doing it. It is kind of like a game or a puzzle. The longer you work on it the more you are into it”. Groele said that he didn’t really have any bad or good things to say about the job. He said he didn’t really find any satisfaction or enjoyment helping the people who hire him in doing his job, but it pays a lot.
Grey Hats: The techies who tread a thin line between good and bad, or hop back and forth from one side to the other for their better interests. Grey hats could just be normal people who dabble in minor fraud schemes or tag websites much like someone would tag a wall with spray paint; a grey hat could be considered a robin hoodesque vigilante or a merc with no moral compass just looking for something to break, and while it does sound serious these aren’t crimes as harsh as some that black hats commit.
Black Hats: The bad guys, the mischievous fiends, the people who just hacked the mainframe by tapping on the keyboard in Command Prompt. Although that last part was a joke commonly used as a movie cliche there is some truth to how easy it is to exploit vulnerabilities in all sorts of programs. Black Hats are criminals that do a great job of this; whether it be selling information, DDOS’ing websites that ticked them off, or exploiting/blackmailing the target and leaving their mark plastered all over. I may have made grey hats and black hats sound similar, and don’t get me wrong they really are, but it is just that black hats commit more heinous crimes that are more severely punished. Black hats love messing with people as seen in a short film relevant to the topic, and while the guy didn’t do anything illegal he did showcase how easy it was to spy on someone today.
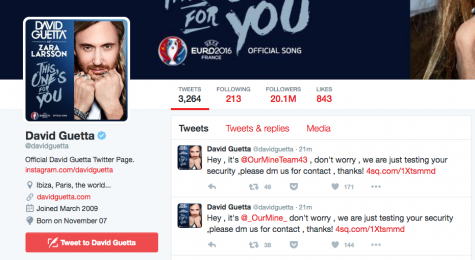
There are groups out there made up of hacktivists, people who hack for political reasons, that prove just how righteous some are about their beliefs. OurMine, a security tech startup/hacker group, forcefully hacks celebrities and businesses, then tries to offer their security services in an attempt to justify their actions. When asked about OurMine Groele responded with, “I don’t approve of OurMine… hacking twitter/social media is small potatoes if you know what I’m saying;” basically bashing them for what is considered small time hacking compared to something that may actually pose a threat to people. I can see why he holds such a view in his line of business.
Script kiddies: Lusers, lamers, and ID:10ts, all of these slang terms describe the people who might know what they did wrong… but don’t know how the program or the programs they have downloaded actually work. Hackers hate them because they ruin their name and professionals laugh at them because of their ignorance. Anyone could be a script kiddie, it isn’t challenging to take someone’s code and destroy a computer or system.
There are many types of hackers out there and this article by no means covers them all, but the market for white hats is growing quickly so throwing yourself out there isn’t a bad idea.
*name changed at the request of interviewee